FwordCTF 2021 Writeup
Background
28 Aug 2021, 01:00 HKT — 29 Aug 2021, 13:00 HKT
Format: Jeopardy
Official URL: https://ctf.fword.tech/
Event organizers: Fword
CTFtime: https://ctftime.org/event/1405
This is the first CTF I participated after I decided to join back the CTF world. Only 2 simple crypto were solved, showing that there is plenty of rooooooooooooooooooom for improvement of my CTF skills.
Challenges
Leaky Blinders - Crypto (100 points)
Challenge :
Get the flag, by order of the leaky fookin blinders..
nc 52.149.135.130 4869
Files :
Solution :
From the decrypt function below, we know that the provided ciphertext will xor with the provided key then perform the standard AES decryption.
def decrypt(cipher, k):
aes = AES.new(k, AES.MODE_ECB)
cipher = xor(cipher, k)
msg = unpad(aes.decrypt(cipher), 16)
return msgThe goal is to provide a ciphertext and key that output “FwordCTF” after the decryption. It is obvious that one can encrypt the word offline and provide the used ciphertext and key to obtain the flag.
Solve:
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
import sys, os, pwc
FLAG = b"FwordCTF{###############################################################}"
key = os.urandom(32)
def encrypt(msg):
aes = AES.new(key, AES.MODE_ECB)
if len(msg) % 16 != 0:
msg = pad(msg, 16)
cipher = aes.encrypt(msg)
cipher = xor(cipher, key)
return cipher
io = pwn.remote("52.149.135.130", 4869)
io.recvuntil(b'> ')
io.sendline('2')
io.sendline(key.hex())
io.sendline(encrypt(FLAG).hex())
io.interactive()FLAG : FwordCTF{N3v3r_x0r_w1thout_r4nd0m1s1ng_th3_k3y_0r_m4yb3_s3cur3_y0ur_c0d3}
Official writeup : The Real Crypto Solution
Boombastic - Crypto (738 points)
Challenge :
A pen and a paper, thats’s all you need to watch the movie.
nc 52.149.135.130 4872
Files :
Solution :
By doing some maths we can recover the value of secret from knowing s, r and p, as shown below (x is secret):
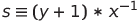
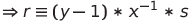
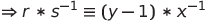
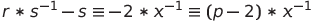

Therefore we can just “Get a ticket” first, calculate the secret and “Enter Cinema”!
Solve:
from Crypto.Util.number import inverse
from json import loads, dumps
import hashlib, sys, os, signal, pwn
def find_secret(msg):
r = int(msg['r'], 16)
s = int(msg['s'], 16)
p = int(msg['p'], 16)
secret = (inverse((r*inverse(s, p)-s),p)*(p-2)) % p
return secret, p
def get_ticket(code, secret, p):
y = int(hashlib.sha256(code.encode()).hexdigest(),16)
r = ((y**2 - 1) * (inverse(secret**2, p))) % p
s = ((1 + y) * (inverse(secret, p))) % p
return {'s': hex(s), 'r': hex(r), 'p': hex(p)}
io = pwn.remote("52.149.135.130", 4872)
io.recvuntil(b'>')
io.sendline(b'2')
io.recvuntil(b'Your ticket : ')
ticket = io.recvuntil(b'}')
io.recvuntil(b'>')
io.sendline(b'1')
io.recvuntil(b'Enter the magic word : ')
secret, p = find_secret(loads(ticket))
ans = dumps(get_ticket("Boombastic", secret, int(p)))
io.sendline(str.encode(ans))
print(io.recvline())
io.close()FLAG : FwordCTF{4ct_l1k3_a_V1P_4nd_b3c0m3_a_V1P}
Official writeup : https://github.com/MehdiBHA/FwordCTF-2021/tree/main/Boombastic
